
Do you still think hackers only attack big companies? Do you still think your company is too small for hackers? As small and medium-sized enterprises (SMEs) begin to embrace digital transformation, the lack of cybersecurity information for SMEs has become the best target for hackers. According to CISCO's Cybersecurity for SMBs:
Asia Pacific Businesses Prepare for Digital Defense report, 56% of SMEs in the Asia-Pacific region (APJC) have experienced cyber security incidents in the past 12 months, and the attack methods are all-too-common items, including DDoS attacks, malware, and social engineering, etc.
# The key factors: budget and human resources
Cymetrics, as a partner of SMEs, aims to provide complete and reasonably priced security assessments. The voice of customers is the development indicator of the product team. After interviews with users, we have summarized five main problems encountered by SMEs in terms of cybersecurity. The rankings are as follows according to the number of times the issue was mentioned during the interview:
TOP 1: Limited Budget
Money is the keyword most mentioned by SME MIS engineers in our interviews. Budget is often the key consideration for a team or company to decide on its cybersecurity configuration. Many MISs spend a lot of time calculating the cost, only hoping to exchange the most efficient package with a limited budget. However, most cybersecurity products are not cheap, which has also become an obstacle for SMEs when protecting their digital assets.
TOP 2: Insufficient cybersecurity human resources
Most of the cybersecurity of SMEs is taken care of by the MIS team. Most of the time, they have already tightened up the management of internal software systems, hardware architecture, and other issues. For cybersecurity, most of them can only passively defend. In SMEs, while relevant personnel can own a comprehensive understanding of the overall cybersecurity situation, there are no additional human resources to solve it.

TOP 3: No professional cybersecurity team, limited cybersecurity knowledge
Cybersecurity is a broad and profound field. SMEs often hope that MIS will cover mountains and seas. In addition to setting up networks and repairing computers, they also need to open the skill tree of cybersecurity. However, in our interviews, we often hear that MIS personnel have to rely heavily on Google as their cybersecurity instructor. Many problems can’t be solved with Google. So they can only “let it go” and wait for the problem to be discovered by hackers.
TOP 4: Cybersecurity is complicated. I don’t know where to start
There are hundreds of cybersecurity products. Should we attack or defend, and to what extent should we defend? An MIS who is not a cybersecurity expert, can only believe what the system integrator or cybersecurity product provider says without a complete understanding of the company's cybersecurity. Cybersecurity issues are different for companies, and nothing can be fixed without the right medicine.
TOP 5: The boss lacks cybersecurity awareness
Finally, the most critical person is the boss. Most SME owners know that cybersecurity "should" be done, but they never did much before being attacked. The most common sentence we heard in user interviews is, "We know that cybersecurity is important, but in the end, it is up to the boss to decide what to use." Before solving the problems above, the cybersecurity awareness of the person in charge is crucial. Without the support of the key person, the business's cybersecurity will be unsatisfactory.
To conclude the problems above, human resources, cybersecurity ability, and budget are the keys to having excellent cybersecurity for SMEs. When the key person is aware of cybersecurity, we recommend SMEs conduct a cybersecurity exposure test on the digital assets first. This way, the company would have a comprehensive understanding of its cybersecurity loopholes and be able to fix them accordingly.
# Wooden bucket theory: water flows out if there is one short wood
The Wooden Bucket Theory (Cannikin Law) is often cited in the cybersecurity field to explain the situation of cybersecurity defense: Suppose there is a bucket made up of boards of uneven length, as long as one of the boards is too short, no matter how long the others are, the water contained in it will flow out. Imagine that the digital assets are the water in the bucket, and each board is the cybersecurity risk. While concentrating cybersecurity resources on certain aspects, the company should check on the status of each risk to effectively protect the company's assets.
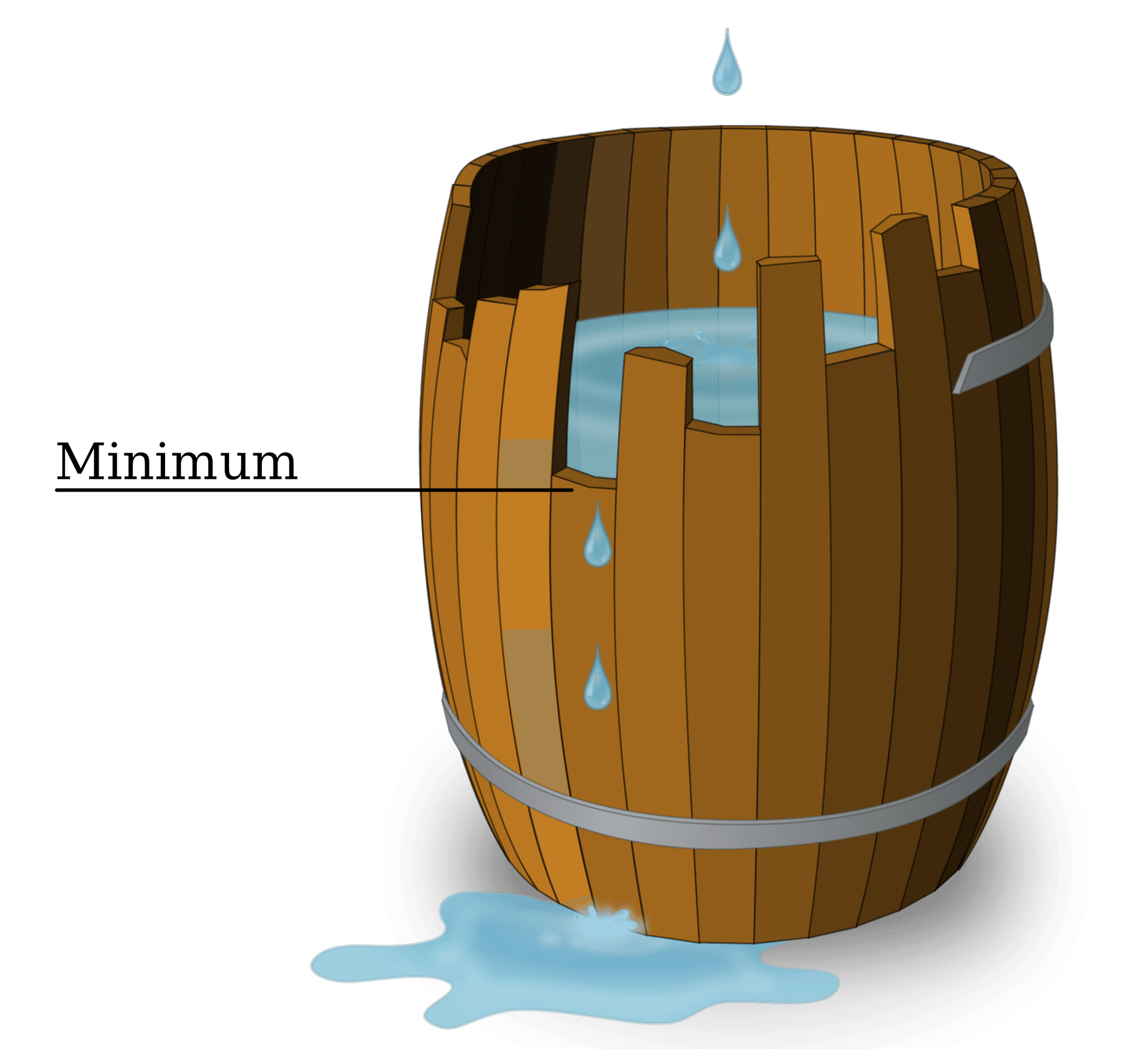
To keep up with hackers, modern cybersecurity strategies should evolve from "compliance-oriented" to "risk-oriented with the perspective of hackers". Security testing improves the gaps between the company’s current cybersecurity status to the ideal ones and turns risks into competitive advantages for enterprises. The best cybersecurity strategy for SMEs is nothing but a comprehensive grasp of hacker thoughts and proactively strengthening defenses for every vulnerability. Thus, the business can most effectively block hackers from the door. If you are interested in the cybersecurity exposure assessment, please contact Cymetrics for further information.
Tag
Recommendation
Discussion(login required)
